Unicode isn't even properly supported on the Codexbecause they have no idea what they're doingAt least make it so we only have to input the code every 3 months, or better yet, don't ask for any codes as long as I don't clear my cookies. I don't get how asking for it every month makes it "safer" at all. Google forces 2FA and I haven't had to enter any codes since a very long time when using gmail. The current solution is pure boomer tech illiteracy insanity.
-
Welcome to rpgcodex.net, a site dedicated to discussing computer based role-playing games in a free and open fashion. We're less strict than other forums, but please refer to the rules.
"This message is awaiting moderator approval": All new users must pass through our moderation queue before they will be able to post normally. Until your account has "passed" your posts will only be visible to yourself (and moderators) until they are approved. Give us a week to get around to approving / deleting / ignoring your mundane opinion on crap before hassling us about it. Once you have passed the moderation period (think of it as a test), you will be able to post normally, just like all the other retards.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
PUBLIC SERVICE ANNOUNCEMENT: 2FA NOW MANDATORY - YOU DON'T NEED A PHONE NUMBER FFS
- Thread starter Crispy
- Start date
- Joined
- Jun 29, 2022
- Messages
- 159
After Hamas is victorious in their struggle against the Zionist oppressor, they will force the Codex admins to remove 2FA.
CHEMS
Scholar
- Joined
- Nov 17, 2020
- Messages
- 1,694
I DON'T WANNA!People still talking about this shit?
Come on guys, once a month you copy-paste a code received via an e-mail into RPGcodex and log.
It's neither complicated or particularly inconvenient.
Your whining about it for so fucking long is beyond embarrassing.
- Joined
- Dec 30, 2023
- Messages
- 18

Folks, help me understand something. The codex is supposed to be filled w/ old bastards from the dark age of the series of tubes we call the internet. Surely hardening the login process from Reddit tranny goons via 2FA is a small price to pay?
If you people are having trouble w/ 2FA management, buy a Macintosh or unplug your routers.
If you people are having trouble w/ 2FA management, buy a Macintosh or unplug your routers.
Peachcurl
Arcane
Oh, isn't that just great. ANOTHER bothersome chore.Folks, help me understand something.
Yes; you see, a notable characteristic of this demographic is violent opposition to any change whatsoever that upsets their daily routine by making things look, feel or behave differently to what they've been used to in the past. This is not limited to 2FA only, which is an actual small inconvenience, but any other change as well.old bastards from the dark age
This is why anything whatsoever that changes on the Codex gets a 50+ page thread of people complaining about it for a few weeks until the next Horrible Change comes along and they can shift to complaining about that. Never a dull moment on the Codex.
- Joined
- Dec 30, 2023
- Messages
- 18

Peach, it’s internet autism like yours that compelled me to sign up for an account and turn 2FA on.Oh, isn't that just great. ANOTHER bothersome chore.Folks, help me understand something.
- Joined
- Dec 30, 2023
- Messages
- 18

I’d speculate one factor for resistance to the use of 2FA is the loss of plausible deniability when certain codex denizens post about Thai lady boys, then can no longer so easily claim to have been hacked.Yes; you see, a notable characteristic of this demographic is violent opposition to any change whatsoever that upsets their daily routine by making things look, feel or behave differently to what they've been used to in the past. This is not limited to 2FA only, which is an actual small inconvenience, but any other change as well.old bastards from the dark age
This is why anything whatsoever that changes on the Codex gets a 50+ page thread of people complaining about it for a few weeks until the next Horrible Change comes along and they can shift to complaining about that. Never a dull moment on the Codex.
Athena
Educated
- Joined
- Sep 19, 2022
- Messages
- 204
The funny thing is that you don't want to be inconvenienced to find a better solution that doesn't annoy the majority of the user base. Of all the possible implementations of 2FA, this is one of the clumsiest I've seen.This is not limited to 2FA only, which is an actual small inconvenience, but any other change as well.
Melcar
Arcane
2 fucks authentication
- Joined
- Dec 30, 2023
- Messages
- 18

2 fucks authentication

We're using the only implementation that XenForo provides. As far as I know, there are no alternatives available, so no, it's not as easy as "just find a better 2FA".The funny thing is that you don't want to be inconvenienced to find a better solution that doesn't annoy the majority of the user base.
You've been here a little over a year and you think you can speak for the majority here?annoy the majority of the user base
You have absolutely no idea what you're talking about.
Athena
Educated
- Joined
- Sep 19, 2022
- Messages
- 204
I'm just going by what people are posting in this thread. Of course, I can't know what the silent majority thinks because, well, they're silent. Maybe make a poll or something, and don't forget to account for the users who left because of 2FA.You've been here a little over a year and you think you can speak for the majority here?annoy the majority of the user base
You have absolutely no idea what you're talking about.
Melcar
Arcane
Next up is dick scanning.
https://haveibeenpwned.com/Passwords
https://github.com/mikepound/pwned-search/blob/master/pwned.py (download) — Client requires
I modified the client to receive passwords on stdin and emit colors—
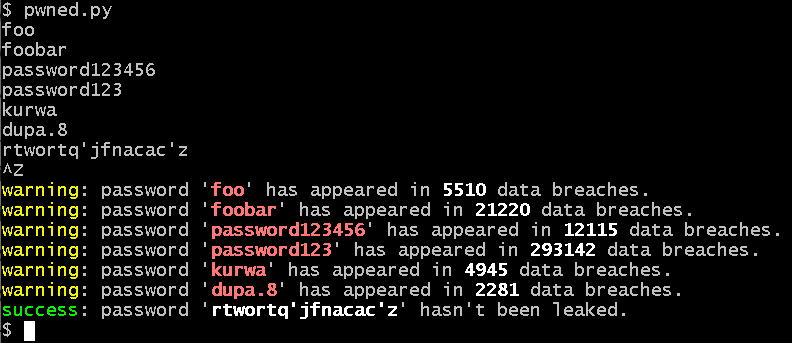
https://github.com/mikepound/pwned-search/blob/master/pwned.py (download) — Client requires
pip install requests first.I modified the client to receive passwords on stdin and emit colors—
Python:
#!/usr/bin/env python
# -*- coding: utf-8 -*-
import hashlib
import requests
import re
import sys
import os
C = {
'header': '\033[95m',
'red': '\033[31m',
'green': '\033[32m',
'cyan': '\033[36m',
'okblue': '\033[94m',
'okcyan': '\033[96m',
'okgreen': '\033[92m',
'warn': '\033[93m',
'fail': '\033[91m',
'end': '\033[0m',
'bold': '\033[1m',
'unbold': '\033[22m',
'underline': '\033[4m',
}
def color(prefix, s):
return "%s%s%s" % (prefix, s, ENDC)
def check_leak(x):
SHA1 = hashlib.sha1(x.encode('utf-8'))
hash_string = SHA1.hexdigest().upper()
prefix = hash_string[0:5]
header = {
'User-Agent': 'password checker'
}
url = "https://api.pwnedpasswords.com/range/{}".format(prefix)
req = requests.get(url, headers=header).content.decode('utf-8')
# split the result twice - each line into key, value
# pairs of hash-postfixes and the usage count.
hashes = dict(t.split(":") for t in req.split('\r\n'))
# add the prefix to the key values (hashes) of the hashes dictionary
hashes = dict((prefix + key, value) for (key, value) in hashes.items())
for item_hash in hashes:
if item_hash == hash_string:
print("{warn}warning{end}: password '{red}{bold}{passwd}{end}'"
" has appeared in {bold}{count}{unbold} data breaches."
#.format(**C))
.format(passwd=x, count=hashes[hash_string], **C))
break
if hash_string != item_hash:
print("{okgreen}success{end}: password '{bold}{passwd}{unbold}'"
" hasn't been leaked.".format(passwd=x, **C))
assert len(sys.argv) == 1
strings = []
for x in sys.stdin:
strings.append(x.strip())
for x in strings:
check_leak(x)
'''
-References-
https://haveibeenpwned.com/API/v3#PwnedPasswords
https://www.troyhunt.com/ive-just-launched-pwned-passwords-version-2/
'''
Last edited:
- Joined
- Jan 16, 2018
- Messages
- 2,876


Exactly, that is how you handle software development as well.Yes; you see, a notable characteristic of this demographic is violent opposition to any change whatsoever that upsets their daily routine by making things look, feel or behave differently to what they've been used to in the past. This is not limited to 2FA only, which is an actual small inconvenience, but any other change as well.old bastards from the dark age
This is why anything whatsoever that changes on the Codex gets a 50+ page thread of people complaining about it for a few weeks until the next Horrible Change comes along and they can shift to complaining about that. Never a dull moment on the Codex.
1. You get requirements, of course you ignore them, because you know better.
2. Then you hack something together that somewhat works.
3 .Then it goes to Testing
4. Then you complain about all the Bugs that were found and blame the Testers
5. You miss the deadline, fucking QA messing with you again.
6. It get's released nonetheless because it would be to expensive to actually fix the issues that were found
7. you get Enduser feedback that it's hardly working or usability is completely arse
8. You blame the endusers, what fucking nerve they have, they simply do not understand how to correctly use it!
9 After emergency meetings it's finally decided to fix the most important issues
10.Requirements get made
-> BACK TO 1.
- Joined
- May 25, 2006
- Messages
- 8,363
Is there really no way in xenforo to configure the 2FA expiration to be longer than 30 days?We're using the only implementation that XenForo provides. As far as I know, there are no alternatives available, so no, it's not as easy as "just find a better 2FA".The funny thing is that you don't want to be inconvenienced to find a better solution that doesn't annoy the majority of the user base.
- Joined
- Jun 18, 2002
- Messages
- 28,575
Not by default. There is a mod I'm looking at though.
https://xenforo.com/community/resources/digitalpoint-security-passkeys.8738/
https://xenforo.com/community/resources/digitalpoint-security-passkeys.8738/
Interesting, googling didn't bring that one up. Way overkill having to install that just to extend 2FA trust days, though. I doubt anyone here would use anything else. Might as well just find where that 30 is defined and change it.
Melcar
Arcane
So mods will fix it?
Viata
Arcane
Just what we could expect from a forum related to rpg.So mods will fix it?
Why isn't the "device" trusted for 30 days after the last login or even a year?
That makes about 5000% more sense. When muh russian hackers get your account credentials, they usually don't get hold of your DEVICE.
That makes about 5000% more sense. When muh russian hackers get your account credentials, they usually don't get hold of your DEVICE.


It is. That's exactly why we have to re-enter our codes every 30 days.Why isn't the "device" trusted for 30 days after the last login
IDIOT.